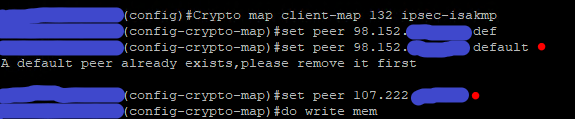
When working with CISCO router based IPSEC VPN tunnels, we might need to enable HA feature for the continuous connectivity with the remote peer. By default, we use just a single peer IP address. But if the remote peer is dead for some reason, we face issues with IPSEC tunnel failure. In order to mitigate that risk, we can use the feature called “default peer” . What it does is, it enable us to define multiple redundant peers instead of a single peer.
The most preference is always given to the “default” peer. If the default peer IP address is unreachable for any reason, the next available peer will be elected as the tunnel peer. The peer status is detected by a feature called “Dead Peer Detection (DPD)”. So, lets jump into the config,
(NOTE: always verify whether these command-lets are supported by the router)
Configuring a Default Peer
enable
configure terminal
crypto map map-name seq-num ipsec-isakmp profile profile-name
set peer ip-address default
exit
Continue reading “Setting up multiple IPSEC VPN peers on Cisco IOS & IOS XE”


