When you work with Cisco Firepower firewall systems, you may come across issues related to ACLs. What happens is Firepower systems drop any remote traffic even if the correct ACLs are in place. To resolve this issue a workaround can be applied.
The parameter is sysopt connection permit-vpn can be enabled. On ASA systems, this is enabled by default. But not on firepower systems. We will look at how we can enable this parameter on Firepower Device Manager (FDM).
Go to FDM GUI > Device > Advanced Configuration > View Configuration
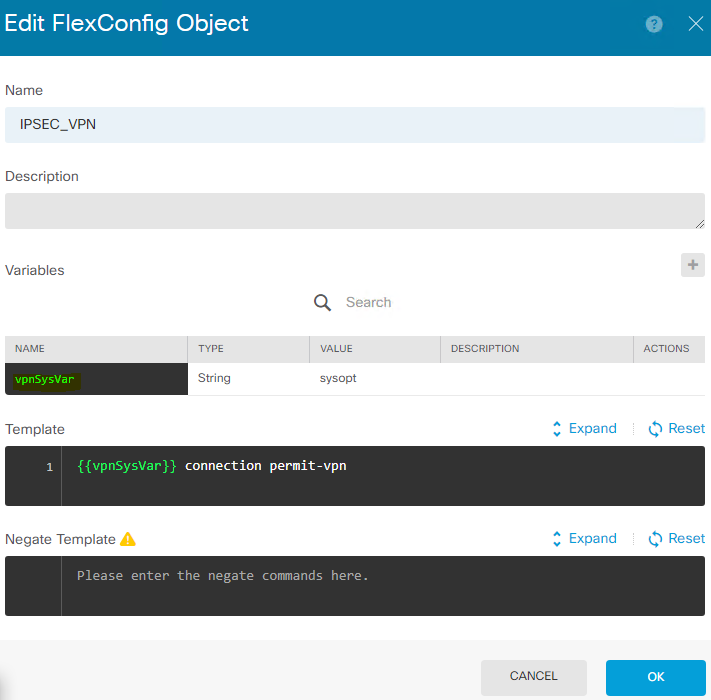
Click on FlexConfig Objects and click on the ‘+’ icon to create a new FlexConfig object, give it a name
Click on the ‘+’ icon for the ‘Variables’ section. Give the variable any name, and select ‘string’ as its type. Enter ‘sysopt’ (without quotes) as the value, and click ok.
In the template section, type {{vpnSysVar}} connection permit-vpn
Go to Flexconfig policy and add the newly created Flexconfig object.
Finally, Save and deploy the changes.

