Due to the cybersecurity compliance requirements, we had to disable insecure SSL and TLS protocol versions. Our infrastructure consists of VMware multi-tenants and F5 LTM as the ADC (Application Delivery Controller). Since the UAGs (Unified Access Gateway) sit behind the F5 LTM, the configuration changes need to be done at the F5 ADC.
There was no proper article written specifically for this purpose. So, I thought of sharing this with the community. Let’s look at the steps involved in the configuration change.
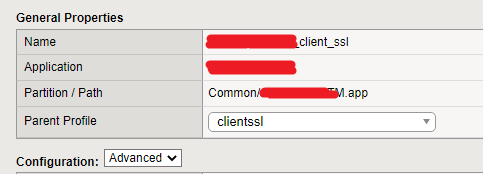
- From the configuration utility, navigate to Local Traffic > Profiles > SSL > Client
- Select the Client SSL profile used in the virtual server, and then change to Advanced
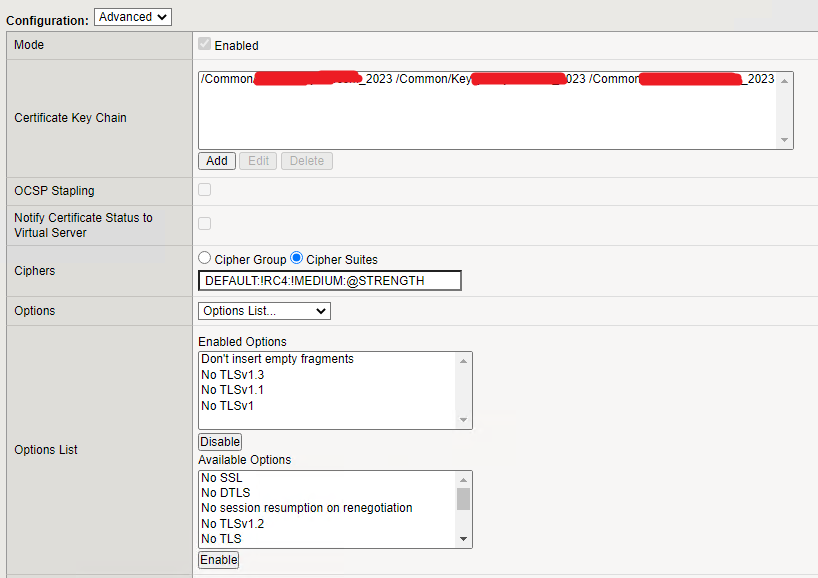
- We need to change 2 fields (Cipers and Enabled Options)
- Under the Ciphers, select Cipher Suites
- In Cipher Suites, you need to change the value to DEFAULT:!RC4:!MEDIUM:@STRENGTH
- Then, under the Enabled Options select only No TLSv1.3, No TLSv1.1, and No TLSv1 (refer to the below image)
- Once you confirm the values, you may save the changes and test the access.
- If you need to confirm the security settings and collect evidence, you can simply test the URL with ssllabs