First of all we will discuss about a common use case with regards to the RDM – Raw Device Mappings,
Microsoft failover clustering service requires to have RDM volumes specially when using the multi host clustering setup (cluster-across-boxes)
In this setup, Physical compatibility mode is being used. By doing this the VM will have more IOPS access than the virtualized storage.
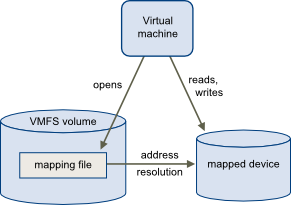
Raw device mapping (RDM) is a mapping file that provides direct access to a LUN on an iscsi or fibre channel storage system for a virtual machine. RDM is basically a Mapping file acts as a proxy for a raw physical storage device placed in a VMFS volume. Virtual Machine can directly access the storage device using RDM and RDM contains metadata which controls the disk access to the physical device. Raw Device Mapping (RDM) gives you some of the advantages of direct access to a physical device while keeping some advantages of a virtual disk in VMFS.
Now, let’s discuss the Migration process of the VM servers with RDM in detail;
Migrating virtual machines with RDMs can be performed in three ways:
- Warm migration (vMotion), with the virtual machine powered on.
- Cold migration, with the virtual machine powered off.
- Storage migration (Storage vMotion), with the virtual machine powered on.
To be honest, this process is a pain and also not an easy task to carry out.
But VMware discusses some of the common questions that arise when migrating virtual machines that use Raw Device Mappings (RDMs).