From architecture perspective, Cisco ASA and FTD (Firepower Threat Defense) operate in different ways. ASA operate at Layer 3/4, whereas FTD operate at Layer 7. Even the CLI behaves in such different ways. So, will look at most important commands which are to be used on Cisco FTD devices.
01. CLI mode for Advanced troubleshooting
By default, you will see something like this.
But in order to run additional commands, you will have to access the CLI. In order to access the CLI, you can simply execute the command system support diagnostic-cli
02. Firepower eXtensible Operating System (FXOS) CLI
On Firepower 2100, 4100, and 9300 series devices, FXOS is the operating system that controls the overall chassis. Depending on the model, you use FXOS for configuration and troubleshooting. From FXOS, you can enter the Firepower Threat Defense CLI using the connect ftd command.
you may either use connect ftd or connect fxos
03. FTD Packet Tracer Utility
The packet tracer will generate virtual packets and it will trigger a packet flow based on your requirement. The command would look like below
packet-tracer input “source interface” “protocol type” “source” “source_subnet” “ICMP code_if ICMP is used” “destination” “destination_subnet”
![]()
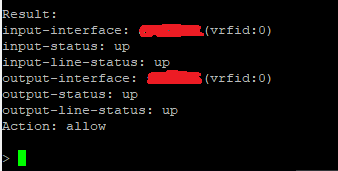
Once you execute the above command, you will be presented with the end results.
04. Run live packet captures on selcted interfaces
First of all, you need to enable packet capture on the selcted interface.
capture “capture_name” interface “source_interface_name” match “protocol” “source_IP Address” “destination_IP Address”
![]()
and then you can see the packet capture by executing the command show capture “name_of_the_capture”
finally, if you are done with the packet capture. you can simply delete the existing captures by executing the command no capture “name_of_the_capture”
![]()
[source: www.cisco.com]

