Very recently, one of our clients raised a concern saying that their application is failing to install with the error “Fatal glibc error: CPU does not support x86-64-v2”. Upon investigation, we found out that this is related to the CPU features. Since we are using VMWare vSphere as the hypervisor, we had only one option. That affected VM is a part of our vSphere Cluster. So, finally, we ended up raising the VMware EVC level to a much higher level (Haswell). Will look at how we can carry out the change.
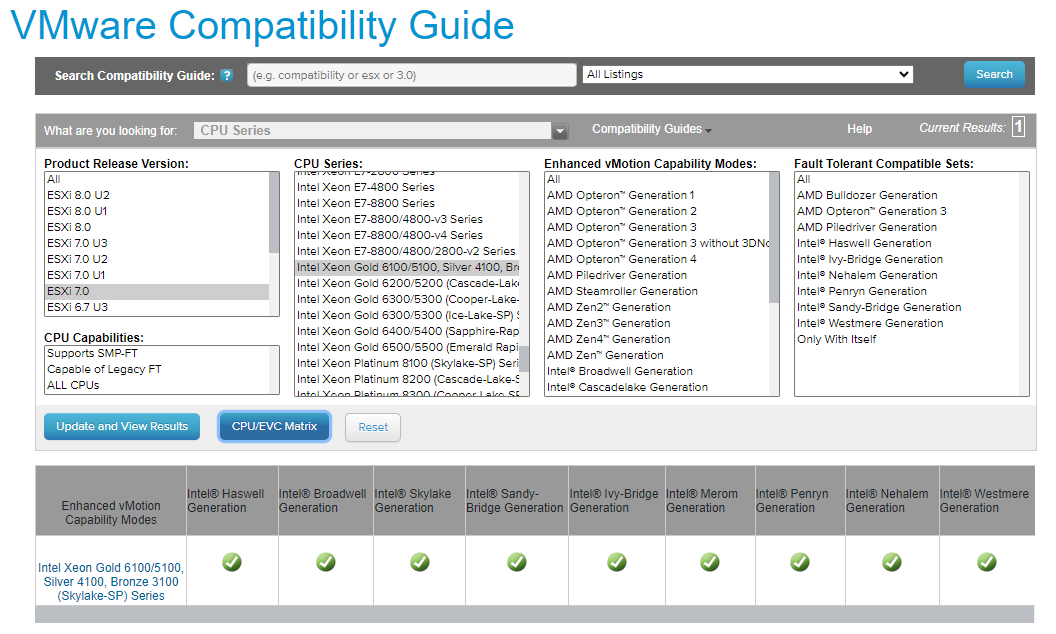
- First of all, make sure that the Processor class supports the latest EVC levels. Browse the VMware Compatibility Guide
- Select CPU from Platform & Compute and pick the correct ESXi version along with the CPU series.
- Click “CPU/EVC Matrix“. In this example, all the EVC levels are been supported.
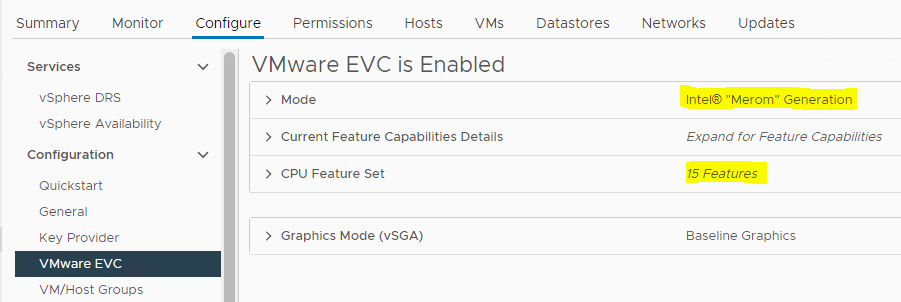
- Then, we can access the vSphere Cluster and look at the EVC configurations.
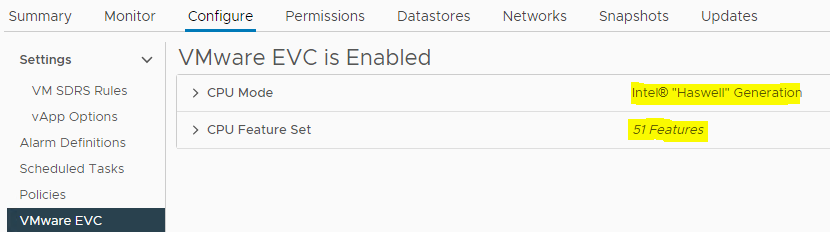
- As you can see, it’s using “Merom” and only supports 15 CPU features.
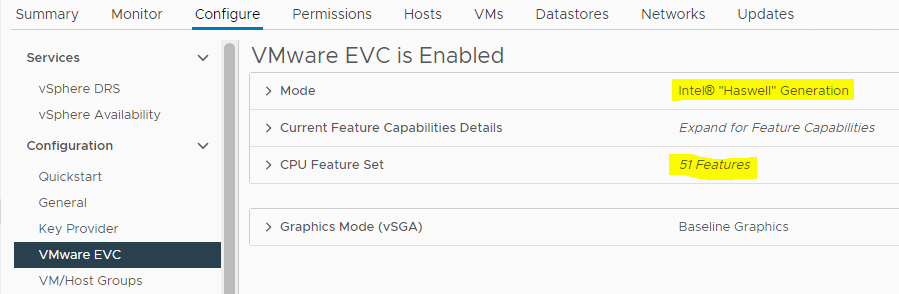
- But, as we discussed we will need advanced CPU features. So, we are going to increase the Cluster EVC level to a much higher value.
- Now, we can see that the EVC level is set to “Haswell” and it supports 51 CPU features.
- Finally, make sure that the VM level EVC is set to the desired level as shown in the below image.