vSphere Standard Switches (vSS)
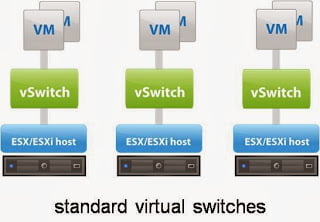
provides network connectivity to hosts and virtual machines. Standard switch can bridge traffic internally between virtual machines in the same VLAN and also link to external networks. Standard switches uses physical Network adapters (NICs) of the ESXi hosts as uplink ports on the standard switch which helps the virtual machines to talk to the outside network. Virtual Machines have it s virtual network adapters (vNICs) that will connect to the port groups on the standard switches. Every port group can use one or more physical NICs of ESXi host attached to it to handle its network traffic.For the Port group with no physical NIC connected to it will allow virtual machines to communicate only with the virtual machines connected on the same port group and will not allow to communicate to external network. In simple terms, vSphere Standard Switches need to be created on each individual hosts.
vSphere Distributed Switch (vDS)
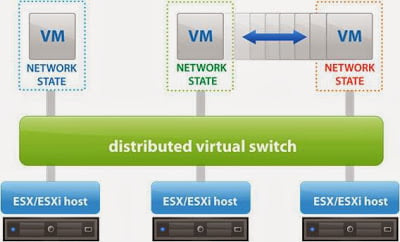
provides centralized management and monitoring of the network configuration of all the ESXi hosts that are associated with the dvswitch. Distributed switch can be created and configured at vCenter server system level and all its settings are propagated to all the hosts that are associated with the switch. dvSwitch is designed to create a consistent switch configuration across every hosts in the datacenter. Network configuration and management for all the hosts that associated with the switch can be performed centralized on the vCenter server system. vDS is only available as part of vSphere Enterprise plus licensing and it’s not created by default.The dvswitch consists of two components, the control plane and the I/O or data plane. vSphere Distributed Switch is also referred as vDS (vSphere Distributed Switch and dvs (Distributed virtual switch).
Continue reading “vSphere Standard Switch vs Distributed switch”