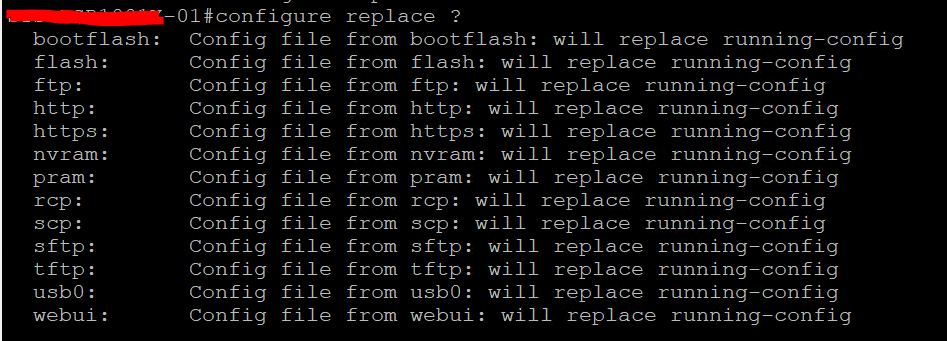
Recently, I had to reconfigure 20+ site-to-site VPN tunnels with IKEv2. Previously, they were running on IKEv1. But after a week time, we had to roll back the changes. One of my work colleague inquired about the rollback options. His plan was to use the command “copy start run“. But if we are looking at a full configuration rollback, we should be using the command “configure replace“.
The copy command MERGE the configuration but never replaces the configuration. This command does not remove commands from the current running configuration that are not present in the source file. So, to overcome this issue, Cisco has released a command for this. The configure replace command provides the capability to replace the current running configuration with any saved Cisco IOS configuration file. This can be used to revert to a previous configuration state, effectively rolling back any configuration changes that were made since the previous configuration state was saved.
In my case, the configuration backup was saved to the Flash: It does not matter where your configuration backup is located.
So, to roll back the changes you may simply run the below command (without []).
configure replace [saved-config-archive]