Once you are done configuring the IPSEC VPN tunnel, we will need to verify the connectivity between sites. So, will discuss these commands in bit detail.
Show crypto isakmp sa
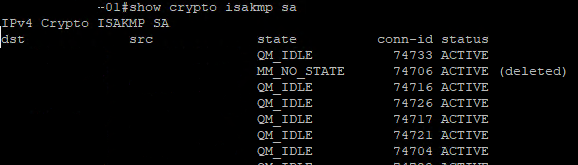
Above command will tell us the status of our ISAKMP negotiations, here are some of the common ISAKMP SA statuses
The following four modes are found in IKE main mode
- MM_NO_STATE – ISAKMP SA process has started but has not continued to form (typically due to a connectivity issue with the peer)
- MM_SA_SETUP – Both peers agree on ISAKMP SA parameters and will move along the process
- MM_KEY_EXCH – Both peers exchange their DH keys and are generating their secret keys. (This state could also mean there is a mis-matched authentication type or PSK, if it does not proceed to the next step)
- MM_KEY_AUTH – ISAKMP SA’s have been authenticated in main mode and will proceed to QM_IDLE immediately
The following three modes are found in IKE aggressive mode
- AG_NO_STATE – ISAKMP SA process has started but has not continued to form (typically do to a connectivity issue with the peer)
- AG_INIT_EXCH – Peers have exchanged their first set of packets in aggressive mode, but have not authenticated yet
- AG_AUTH – ISAKMP SA’s have been authenticated in aggressive mode and will proceed to QM_IDLE immediately
The following mode is found in IKE Quick Mode, phase 2
- QM_IDLE – The ISAKMP SA is idle and authenticated
Please follow and like us:

