Cybersecurity frameworks are the key starting point for any organization that wants to meet regulatory compliance and demonstrate security readiness to leadership. Still, compliance is hard, and every organization struggles to prove it. Today, we will be looking at how ATT&CK frameowrk helps to achieve this goal.
In ATT&CK framework, there are 2 some what related terms called TACTICS & TECHNIQUES. Tactics represent the “why” of an ATT&CK technique or sub-technique. It is the adversary’s tactical goal: the reason for performing an action, where as Techniques represent “how” an adversary achieves a tactical goal by performing an action.
With ATT&CK framework, we can do many things. but today we will be looking at defensive control mapping. Defensive controls can carry well-understood meaning when referenced against the ATT&CK tactics and techniques they apply to. ATT&CK offers really cool applications, such as ATT&CK Navigator. This provides the ability for users to define layers – custom views of an ATT&CK matrix – for example, showing just the techniques for a particular platform, highlighting techniques a specific adversary has been known to use, creating heat maps for heavily used techniques, or visualizing defensive coverage. Layers can be created interactively within the Navigator or generated programmatically and then visualized via the Navigator.
The below video gives a brief walktrough on ATT&CK Navigator
Once you get familar with the above solution, you may start with predefined NIST control templates (which is on Github).
Having access to all the resources, you can pull out the relavent controls. When working with the solution, you need to keep in mind the below points. Below is the set of steps that needs to be done.
Step 01: Access ATT&CK Navigator and select Open Existing Layer > Load from URL
Step 02: Access control framewor, hosted on Github and then select as appropriate (in this example, we have used nist800-53-r4/layers/by_family/Access_Control/AC-10.json)
Step 03: Open up the json file and switch to RAW view
Step 04: Copy the URL and load it to ATT&CK Navigator
Step 05: You will end up with a sheet, something similar to below. using the control mapping, you can easily identify/implement controls as appropriate.
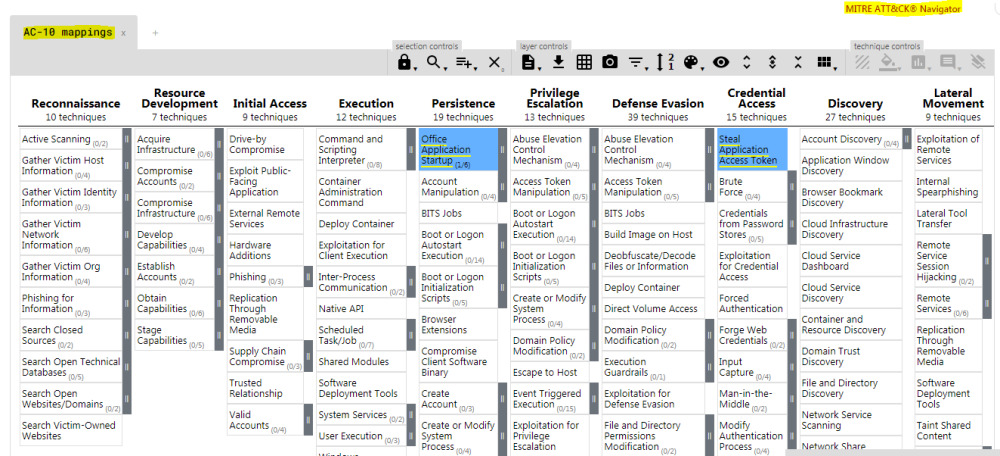
[source: https://attack.mitre.org]