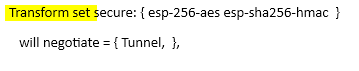Recently, I had to reconfigure all the IPSEC site-to-site tunnels with more secure encryption and authentication. So, the choice was to use IKEv2 along with a more secure IKEv2 proposal and a transform set. First of all, you will need to create both an IKEv2 proposal and a transform set. In this example, I have used the below parameters.
IKEv2 proposal
Once you are done with the above configuration, you can proceed to tenant-specific configurations.
- TT – Denotes the Tenant
- L – Denotes the local peer IP
- P – Denotes the remote peer IP
- KK – Denotes the pre-shared key
- ACL– Denotes the ACL
- G – Denotes the local gateway (has internet access)
- N – Denotes the tenant/VRF number
Below is the configuration.
crypto ikev2 policy TenantTT-policy
match address local L.L.L.L
proposal secure
exit
crypto ikev2 keyring TenantTT-key
peer P.P.P.P
address P.P.P.P
pre-shared-key KK
exit
exit
crypto ikev2 profile TenantTT-profile
ivrf TenantTT-vrf
match address local L.L.L.L
match identity remote address P.P.P.P 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local TenantTT-key
lifetime 28800
dpd 10 5 on-demand
exit
crypto map Tenant-map N ipsec-isakmp
set peer P.P.P.P
set transform-set secure
set ikev2-profile TenantTT-profile
match address ACL
set security-association lifetime seconds 28800
reverse-route remote-peer G.G.G.G static
set pfs group14